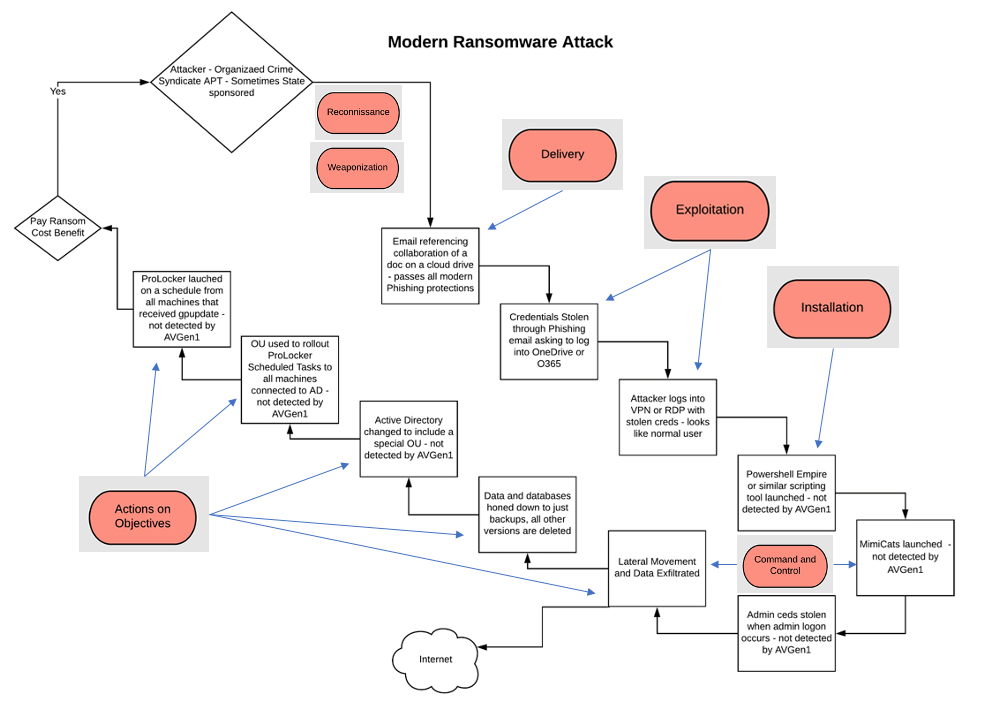
What are cybercriminals after? Money, data, and volume. All three of these points earn the adversary a ticket to their reason for infecting devices in the first place: money. Ransomware, known for its destructive nature, works to encrypt important files that are needed for everyday job functions or contain sensitive data.
Cybercriminals will first gain access to your network either through internet-facing vulnerabilities, such as unpatched Remote Desktop Protocols (RDP), or by an employee clicking on links or downloading a malicious attachment in a phishing email. Cybercriminals will usually drop ransomware on their way out of a system after residing in your network collecting data for a while beforehand. The attacker will then ask for a payment to, allegedly, unencrypt the files and return them back to a normal state.
Unfortunately, being dealt a hand that contains ransomware is usually just the tip of the iceberg for organizations. Since an attacker typically remains in your network undetected between 40 and 200 days, the risk to your organization's data extends beyond being unable to use your computers and networks; today's ransomware often means a full-scale data breach.
Combating a ransomware scenario can be intense and stressful, so most organizations agree that it is better to stop the attack from happening in the first place. Below you will find the top six controls that can be put in place to protect your organization's network and data from a ransomware attack.
Top Controls
Backup, Backup, Backup
It's important to note that backing up your network's data will not prevent a ransomware attack in the future, but doing so will make the situation abundantly less stressful. It's been said that there are two types of people in this world: 1) those who back up their data, and 2) those who wish they would have. It is a good rule of thumb to stick with the 3-2-1 rule. Have at least THREE copies of data, store your backups on TWO different types of media, and keep ONE backup offsite; in other words, keep one copy of the data air-gapped. Creating an "air-gapped" backup would make it very difficult for an attacker to infect this copy of your data with ransomware.
If you diligently back up data, you will ensure that, worst-case scenario, you can wipe the infected device(s) and restore with the backed-up data.
Endpoint Protection with Scripting Control
When it comes to today's current anti-virus or endpoint protection solutions, there are two types of solutions:
- Traditional, signature-based anti-virus/endpoint protection solutions that rely on a known "signature" to identify if a file is potentially "malicious"; or
- Modern, behavior-based anti-virus solutions that look at the code of a file to determine what actions the file will look to take when executed.
While there are pros and cons to each, modern behavior-based anti-virus solutions will handle and identify unknown and unidentified threats, rather than relying on known-bad signatures to prevent potential cyber incidents.
It's strongly recommended that you use a modern, behavior-based solution with second-generation detection capabilities, including scripting control. Keep in mind, some providers claim their product has scripting control consistently fail to detect Powershell scripts running on your network. Applications lacking scripting detection will not be helpful in the event an attacker uses the Powershell tool to create scripts that automate attacks. Your anti-virus solution should be configured to the highest level of security, alerting, and protection. These controls would be able to stop any scripts that would attempt to run without the user's permission. Modern, behavior-based anti-virus solutions should also alert the user if any red flags (malicious behavior) are detected on your devices.
Multi-Factor Authentication
Multi-Factor Authentication (MFA) is an authentication method in which a user is granted access to an application only after allowing two or more pieces of evidence to the authentication mechanism, such as an SMS code, soft token, or hard token. When enabled on a system, MFA would prompt the user if a malicious adversary tried to log in to an account, since the attacker should not have access to your smartphone (SMS or soft token) or hard token (physical device).
Not only would implementing MFA help prevent a ransomware attack, but doing so would mitigate the risk to various other cyberattacks as well, such as credential stuffing, business email account takeover, and phishing attacks. However, just like with every other control, MFA has its drawbacks. You must train employees only to provide authentication factors when they know they are logging in themselves.
The most common failure of MFA is user-error, specifically when a user approves an MFA push-notification on his/her smartphone, but the user is not themselves logging in to an application. Rather, a cybercriminal has obtained the user's credentials and is attempting to log in, and the user approves this login unknowingly. If a user authorizes an adversary's attempt to log into their account, there is no stopping the attacker from accessing the account.
Security Awareness Training
Employees are your first line of defense and are known as the "human firewall." It is important to educate workers of potentially malicious email attachments, links, and other methods of spreading ransomware – including how to identify phishing emails and what to do if they receive or click on something in a phishing email. Phishing emails are still the #1 delivery vehicle for malware, and training your people to handle phishing emails properly may be one of the most important things you can do to mitigate your risk.
Security awareness training should also include educating employees on what to avoid when downloading content from untrusted sites, as well as not connecting unknown equipment to devices, such as USBs. It is a great idea to not only train and educate employees, but to test them, too. Providing workers with social engineering and phishing tests helps expose the employees to potential cyber threats (in a controlled manner). The more an employee is educated and tested, the better the chance they will report phishing emails or suspicious activity.
Email Controls
Email sandboxing along with Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) are impactful controls that can be put in place to protect your network against a ransomware attack.
Email sandboxing, which automatically tests links and attachments in an email in a secure environment before your users receive the email, adds a layer of security and lessens the chances of an employee clicking on a malicious link. The Advanced Persistent Threat subscription to Office 365, which implements the Safe Links and Safe Attachments sandbox controls, is an excellent example of how email sandboxing can protect your organization from email threats.
SPF, DKIM, and DMARC all help authenticate senders using an organization's specific domain. SPF prevents hackers from sending emails on behalf of an organization's domain. In addition to SPF, DKIM checks if an email was truly sent by the owner of that domain. DMARC uses both SPF and DKIM to determine the authenticity of the content of an email message. SPF, DKIM, and DMARC are typically free additions to your email system that can make a significant impact on the amount of junk or phishing email your organization receives.
Egress Firewall Whitelisting with Geolocation IP Blocking
Egress firewall whitelisting examines all outbound traffic from your network to the internet (at the firewall level) and only allows information to leave the network if your organization's IT administrator's requirements are met. Egress firewall whitelisting works best with geolocation IP blocking, which blocks activity to IP addresses associated with geographical locations in which your organization does not do business or wants to block intentionally (like certain foreign countries known for cybercrime). Blocking traffic to certain regions and countries while examining the traffic that leaves the network in the first place is an important control that would notify the organization if a ransomware scenario is unfolding
Ransomware Attack: What Steps to Take
There is no 100% guarantee that an organization will thwart every ransomware scenario, even with all these controls in place. In the event a ransomware scenario does happen, every company should have an Incident Response Playbook scenario on how to handle ransomware, just in case.
Preparation
To prepare for any cyberattack, organizations must put certain controls in place. Some great controls an organization can consider are listed above, but for more additional information, check out SBS's article: Top 5 Most Common Incident Response Scenarios. This article details the most common incident response scenarios and how to protect, detect, and respond accordingly.
Detection
A question that all organizations must ask themselves is:" If there was a cybercriminal in our network, would we know?" Detecting an incident can be one of the biggest challenges for organizations, which is why it is important to identify Key Risk Indicators (KRI) and Indicators of Compromise (IoC) that can focus your attention to key alerts associated with ransomware or a network compromise. KRIs and IoCs are the key to learning what level of traffic is normal for the organization versus what is abnormal. For more in-depth information on KRIs and IoCs, refer to this article by SBS: Indicators of Compromise.
Contain
First and foremost: contain the attack. It is important to deny the attacker any access they have to the network. If the attacker cannot access the network, they cannot access your data. If egress firewall whitelisting has not been implemented prior to detecting an incident, the best thing you can do would be to deploy this control immediately to contain the incident. Doing so will allow you to examine the data leaving the network, ensure that data is supposed to be leaving your network, and ensure your data is sent to the appropriate location(s)/IPs.
Eradication
During this step, our objective is to destroy the attacker's capability on the hosts. To do so, ensure your organization implements Host-Based Intrusion Prevention with Scripting Control. If scripting capabilities can be detected and prevented on your devices, the ransomware attack can be stopped or even blocked.
Recover
If you have not already done so, implement controls to prevent the attacker from compromising your accounts and network again. To recover from a network compromise or ransomware attack, implement controls that were discussed earlier in the article, such as Multi-Factor Authentication (MFA), email sandboxing with SPF, DKIM, and DMARC, and country code blocking on firewalls and cloud resources.
Lessons Learned
The most important (and often skipped) step after an incident has occurred is to hold a lessons learned discussion. Assemble your organization's IT Committee and incident response team to review the details of the incident scenario. Go through what vendors were contacted, what problems the team(s) encountered, and what the organization can learn from this experience. Be sure to keep up to date with new controls that were put in place, and consistently communicate with your team(s) and your executive team on the status of these controls.
It is important to remember that the world of digital forensics and incident response is an ongoing cycle: the process never comes to an end. Start by implementing controls to prevent attacks and monitor your network to ensure all traffic falls within normal levels. When red flags arise on your network, the incident response process begins. After the incident is contained and eradicated, the organization can then recover and hold a lessons-learned meeting. Cybersecurity is a full-time job, and preventing, containing, eradicating, and recovering from attacks should be no different.